 Radio Frequency Identification (RFID) technology represents a significant advancement in automatic identification methods, leveraging radio waves for seamless two-way communication. This allows for the identification of objects and the exchange of data without physical contact. Key benefits include the ability to recognize multiple targets simultaneously, track moving objects, and enable real-time remote monitoring and management. Communication distances can vary from a few centimeters up to several meters, depending on the setup. Its robustness lies in its adaptability to different environments, round-the-clock functionality, non-contact identification, and its capacity to penetrate non-metallic materials while maintaining strong interference resistance.
In recent years, with the increasing number of cars becoming a common household item in China, vehicle management has become a growing concern. One of the central challenges in managing vehicles effectively is accurate identification. By integrating RFID technology into access control systems, we can achieve swift and dependable vehicle recognition, significantly enhancing the efficiency and intelligence of security management.
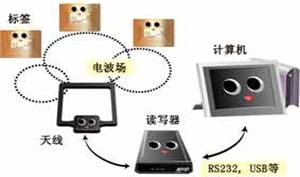
The hardware components of an RFID-based access control system consist of six essential elements: vehicle-mounted electronic tags, car coils, RF interfaces, signal processors, control systems, and management systems.
Firstly, the electronic tag, often referred to as a transponder, contains critical information about the vehicle and its owner. Installed passively on the vehicle, it sends stored data to the reader when within the microwave query signal's coverage area, with an effective reading distance of 6 to 10 meters.
Secondly, the reader comprises two primary modules: the RF interface and the signal processing module. The RF interface handles both sending and receiving signals, converting command signals into microwave signals and vice versa. Meanwhile, the signal processing module focuses on encoding commands and decoding data signals from the electronic tag, ensuring smooth communication between the tag and the management system.
The management system serves as the brain of the operation, tasked with processing user information, electronic tag data, and control system details. It operates based on user instructions, communicates with the control system, and can connect to a security center via a network.
The control system ensures the gate mechanisms respond correctly to commands, feeding back gate statuses to the management system. For instance, upon verifying the legality of a vehicle’s electronic tag, it sends a signal to open the gate.
Additionally, car sensors use coils to detect vehicles based on electromagnetic principles. These detectors are sensitive enough to recognize vehicles passing over or stopping near an embedded loop coil, sending precise signals to the system.
On the software side, the system uses C language for signal processing and Visual C++ (VC) for system management, with Microsoft SQL Server 2000 as the database backend. The workflow begins with initialization, followed by the reader sending inquiry signals at regular intervals. Once the electronic tag responds, the system performs anti-collision processing, decodes the data, and verifies it against the database. If the data matches, the system signals the control system to open the gate; otherwise, an alert is triggered.
The software also features dual-card verification, where two RFID cards must be present for access approval, adding an extra layer of security. The system logs every entry and exit, preventing tampering with records, aiding in statistical analysis and report generation.
Temporary visitors receive special cards for billing purposes, with fees automatically calculated based on their stay. Overall, this RFID-enabled access control system not only expedites vehicle movement but also provides enhanced security and real-time monitoring capabilities, making community and parking lot management more efficient and user-friendly.
In summary, applying RFID technology in access control systems offers numerous advantages, including time-saving measures, improved traffic flow, and enhanced security. It ensures accurate vehicle and owner identification, maintaining regional safety and offering a more sophisticated approach to managing communities and parking facilities.
Radio Frequency Identification (RFID) technology represents a significant advancement in automatic identification methods, leveraging radio waves for seamless two-way communication. This allows for the identification of objects and the exchange of data without physical contact. Key benefits include the ability to recognize multiple targets simultaneously, track moving objects, and enable real-time remote monitoring and management. Communication distances can vary from a few centimeters up to several meters, depending on the setup. Its robustness lies in its adaptability to different environments, round-the-clock functionality, non-contact identification, and its capacity to penetrate non-metallic materials while maintaining strong interference resistance.
In recent years, with the increasing number of cars becoming a common household item in China, vehicle management has become a growing concern. One of the central challenges in managing vehicles effectively is accurate identification. By integrating RFID technology into access control systems, we can achieve swift and dependable vehicle recognition, significantly enhancing the efficiency and intelligence of security management.
The hardware components of an RFID-based access control system consist of six essential elements: vehicle-mounted electronic tags, car coils, RF interfaces, signal processors, control systems, and management systems.
Firstly, the electronic tag, often referred to as a transponder, contains critical information about the vehicle and its owner. Installed passively on the vehicle, it sends stored data to the reader when within the microwave query signal's coverage area, with an effective reading distance of 6 to 10 meters.
Secondly, the reader comprises two primary modules: the RF interface and the signal processing module. The RF interface handles both sending and receiving signals, converting command signals into microwave signals and vice versa. Meanwhile, the signal processing module focuses on encoding commands and decoding data signals from the electronic tag, ensuring smooth communication between the tag and the management system.
The management system serves as the brain of the operation, tasked with processing user information, electronic tag data, and control system details. It operates based on user instructions, communicates with the control system, and can connect to a security center via a network.
The control system ensures the gate mechanisms respond correctly to commands, feeding back gate statuses to the management system. For instance, upon verifying the legality of a vehicle’s electronic tag, it sends a signal to open the gate.
Additionally, car sensors use coils to detect vehicles based on electromagnetic principles. These detectors are sensitive enough to recognize vehicles passing over or stopping near an embedded loop coil, sending precise signals to the system.
On the software side, the system uses C language for signal processing and Visual C++ (VC) for system management, with Microsoft SQL Server 2000 as the database backend. The workflow begins with initialization, followed by the reader sending inquiry signals at regular intervals. Once the electronic tag responds, the system performs anti-collision processing, decodes the data, and verifies it against the database. If the data matches, the system signals the control system to open the gate; otherwise, an alert is triggered.
The software also features dual-card verification, where two RFID cards must be present for access approval, adding an extra layer of security. The system logs every entry and exit, preventing tampering with records, aiding in statistical analysis and report generation.
Temporary visitors receive special cards for billing purposes, with fees automatically calculated based on their stay. Overall, this RFID-enabled access control system not only expedites vehicle movement but also provides enhanced security and real-time monitoring capabilities, making community and parking lot management more efficient and user-friendly.
In summary, applying RFID technology in access control systems offers numerous advantages, including time-saving measures, improved traffic flow, and enhanced security. It ensures accurate vehicle and owner identification, maintaining regional safety and offering a more sophisticated approach to managing communities and parking facilities.
LED Downlight
LED downlight ,with LEDER technology's smooth design is an enhanced and modernized retrofit light. Using a secure and reliable installation method, this light is compatible with housing that features interior spring bracket holders.
Built with steady dimmable technology, and compatible with most modern dimmers including wireless systems. LED Downlight is an especially good choice for anyone looking for a lamp which is elegant in an understated way. If you want an LED Downlight that discreetly keeps itself out of the way, yet looks great once you actually pay attention to it, you have definitely come to the right place. This LED Downlight will do its job very well.
Features:
• Grace design
• Easy to install
• Excellent power saving
• Suitable for operation at low temperature
• Color temperature :3000K-6000K
• Body color can be customized as RAL Code
• Type of protection: IP20 / IP65 (Some models)
• Warranty: 3 ~ 5 years
Our Downlight is compatible with dimmer switches, so you can always get just the right light for dinner or game night. Bring effortless light into your kitchen, bathroom, or living room with this.
We have rich production experience in lighting.Except LED Downlight , we also offered other product in Indoor Lighting .Such as :
LED Panel Light , Track Light , Linear Light ,Wall Light , LED Strip Light , LED Tube Light , Cabinet Light , LED Bulb , LED Ceiling Light as so on .
Recessed Downlight,LED Recessed Downlight,Halo Ultra Thin Downlight,Surface Mounted Downlight
LEDER LIGHTING CO.,LTD , https://www.lederlight.com